At present, the mainstream relational databases in the world, such as Oracle, Sybase, Microsoft SQL server and IBM DB2 / Informix, have the following characteristics: user account and password, verification system, priority model and special permission of control database, built-in commands (stored procedures, triggers, etc.), unique script and programming language (e.g. PL / SQL, transaction SQL, OEMC, etc.) , middleware, network protocol, powerful database management utilities and development tools. Security measures in the database field usually include: identity identification and authentication, independent access control and mandatory access control, secure transmission, system audit, database storage encryption, etc. only by integrating all aspects of security can a highly secure system be ensured.
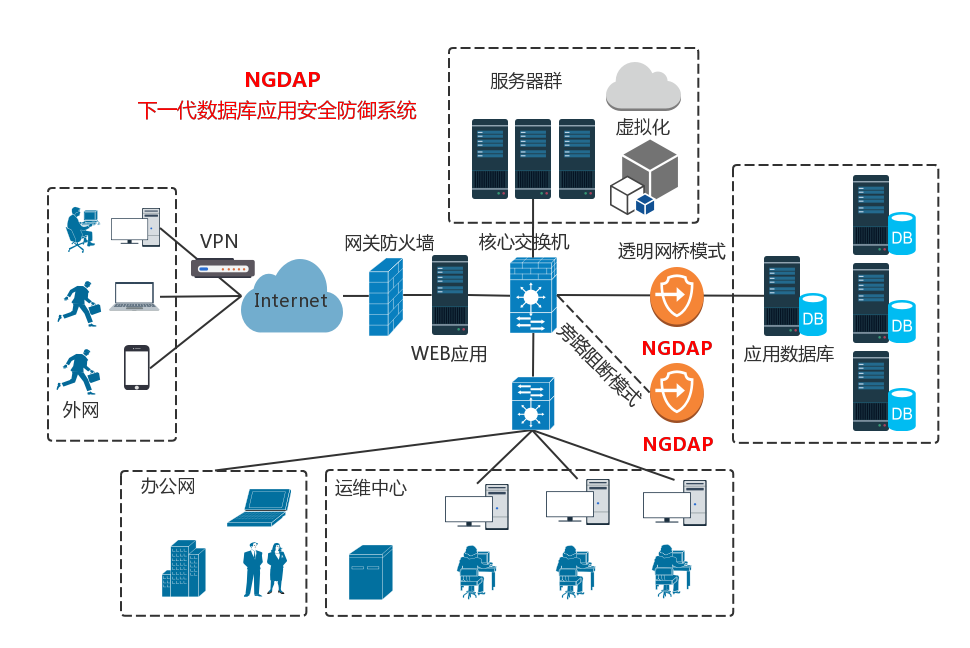
Palladium next generation database application security defense system (ngdap) It is a new generation of data protection system developed by Hangzhou Palladium Network Technology Co., Ltd. ngdap collects, analyzes and identifies the data flow accessing the database. It monitors the operation status of the database in real time, records a variety of database access behaviors, finds abnormal access to the database and blocks it in time.
Network firewall
The database network firewall is mainly based on the control of network behavior and is realized based on TCP quintuple. It carries out policy control according to the source address, target address, source port, target port and transport layer protocol in the quintuple.
Access firewall
Solidify access access rules through self-learning of white list (automatically learn the five elements of database access behavior - access source address exception, access source host name exception, access source user name exception, access tool name exception, login account name exception, solidify security rules) , the unmatched database access behavior will carry out real-time early warning and block the session. Without affecting the performance and modifying the database, it will continuously track all database operations to identify unauthorized or suspicious activities and block them in time, so as to avoid network attacks on the database and fundamentally solve the threat of malicious access to the database.
Behavior firewall
It can accurately track the user's SQL statement commands, control the source, target database, target table and specified behavior, and prevent high-risk illegal operations and misoperations.
Service firewall
In the learning phase, it will record, analyze and count the query requests sent by all applications, and automatically add them to the white list. Users can confirm and adjust the contents of the white list. After switching to the active defense mode, the database firewall will first standardize the request data, and then send the processed data to the pattern matching engine to match the white name Compare the data in the order. If it matches the relevant rules, it is considered a legal request, and the data will be passed to the real database for query and finally returned to the application; if it does not match the relevant rules, it will give an alarm or block the response to completely solve SQL injection, apt and other attacks.